At Rev, Security Comes First
At Rev, we understand that your content is invaluable and needs to be protected. That's why we've built our platform with security at its core, ensuring that every transcript, every file, and every interview is protected by industry-leading security measures.
How Rev Keeps Your Content Safe and Secure
Enterprise-Grade Security
We safeguard your account with multiple layers of protection, giving you peace of mind every time you log in. SSO, MFA, and Domain Claiming ensure that only authorized users can access your sensitive information.
File Protection and Encryption
Your files are protected by industry best-practice standards (like TLS and S3 SSE encryption), both during transmission and storage. Rev backs up critical system data multiple times per day to prevent data loss or corruption.
Industry-Leading Compliance
We adhere to global data protection regulations, ensuring that your data is handled in compliance with the strictest standards, including CJIS, HIPAA*, SOC 2 Type II compliance, and our SOC 3 report is available for review.
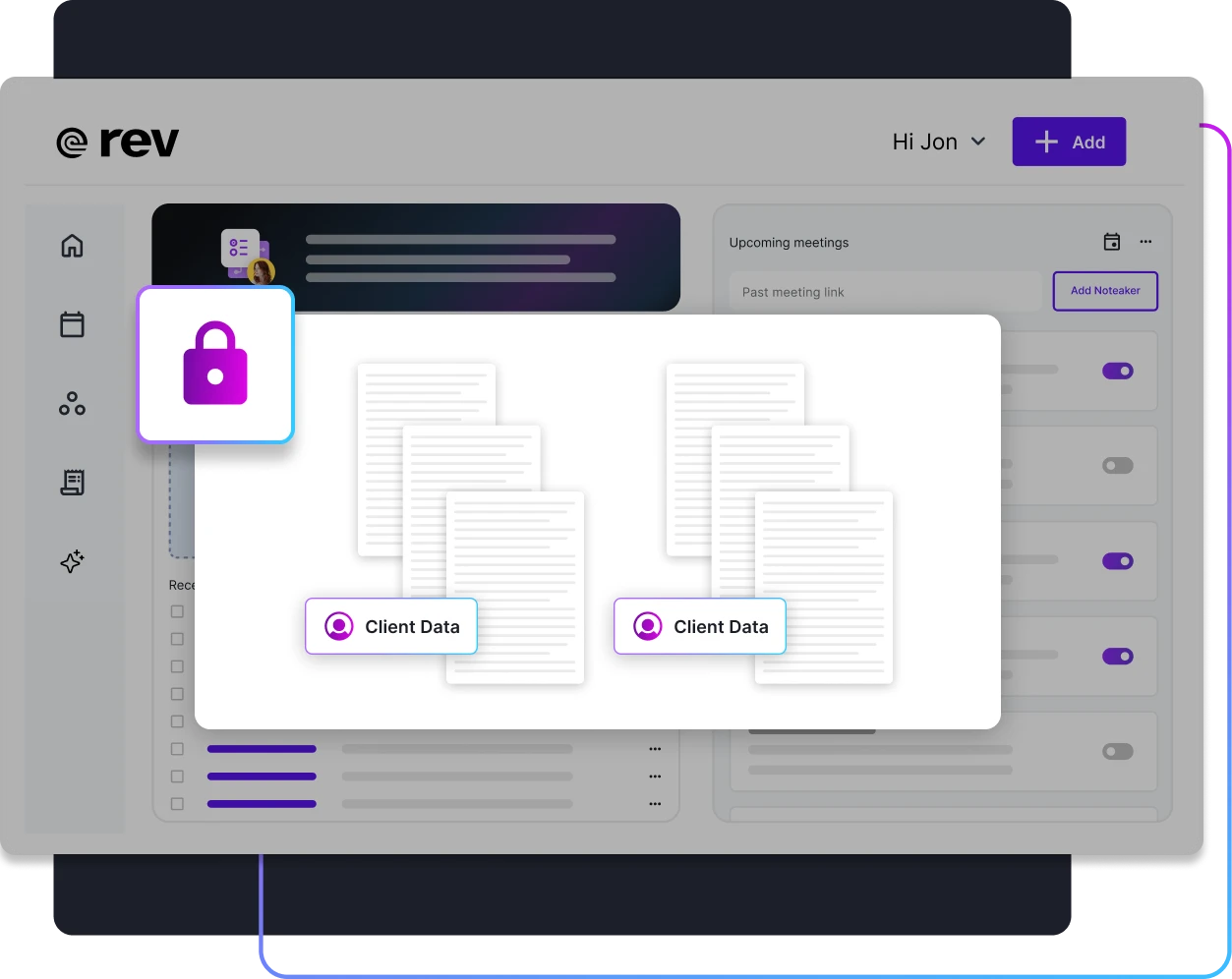
File Sharing Permissions
Control who can access your files with our comprehensive sharing and permission settings. Your data can never be found publicly through search engines, and only users with a link or invitation can view or download your files.
Freelance Transcriptionist Validation
Our human transcriptionists undergo rigorous vetting, including ID verification and NDAs, to ensure the confidentiality of your content
Data Privacy
We treat your data with the utmost respect, implementing strict policies, including GDPR compliance, to protect your privacy and never training external LLMs on your data.
Account Security
Streamline your login process while enhancing security with our SSO integration, for any enterprise plan, no matter the size.

Add an extra layer of protection to your account with our easy-to-use MFA options.

Take control of your account by claiming and managing your domain, authorizing users, and blocking unauthorized users.




File Protection and Encryption
Your files are protected by industry best-practice standards (like TLS and S3 SSE encryption using AES), both during transmission and storage.

We use Amazon's server-side encryption (S3 SSE) to protect your data at rest.


Industry-Leading Compliance
Our systems and processes are regularly audited to meet strict security standards.

Your payment information is processed securely through PCI-compliant systems.

Rev's enterprise tier provides HIPAA-compliant transcription services to protect sensitive healthcare data.

Rev's unlimited plan provides CJIS-compliant transcription services to protect sensitive criminal justice data.





File Sharing and Permissions
Your files are never shared publicly, can’t be found through search, and can only be shared with direct access granting, protecting your sensitive information. In addition, we'll never train external LLMs on your data.

Set precise access levels for each user, maintaining control over your content.

Collaborate safely with team members in controlled, secure environments.




Ongoing Freelancer Verification
All transcriptionists' identities are thoroughly verified before they can access any work.

Every transcriptionist signs a strict NDA, legally binding them to protect your information.

We regularly review transcriptionist performance and identity verification to maintain the highest standards of security and quality.




Data Privacy
We never use your content to train external AI models, ensuring your data remains truly yours.

Our services are designed to help you meet your GDPR obligations effortlessly. More information on how Rev complies with privacy regulations can be found in Rev’s Data Processing Addendum and Privacy Policy.

Rev safeguards PHI through with our enterprise-ready HIPAA* compliance, including end-to-end encryption and secure file handling.




Secure Your Data With Rev
Ready to see what it looks like to store your team’s important meetings, conversations, and interviews in a platform with state-of-the-art security and privacy measures?
Security FAQ
How does Rev Ensure the Security of My Account?
Rev offers multiple layers of account security. We support Single Sign-On (SSO) using SAML 2.0, which can be enforced across a domain or team. We also offer Multi-Factor Authentication (MFA) as an optional setting for all user accounts. Additionally, we provide domain claiming, allowing organizations to manage access across their domain.
What Encryption Methods Does Rev Use To Protect My Files?
Rev uses industry-standard encryption methods to protect your files both in transit and at rest. We employ TLS 1.2 and 1.3 for data in transit, ensuring secure communication between Rev servers and our customers. For data at rest, we use Amazon's S3 SSE (Server-Side Encryption) with unique keys for all buckets and objects.
Is Rev Compliant With International Data Protection Regulations?
Yes, Rev is compliant with key international regulations. We are GDPR compliant and maintain PCI compliance as a merchant for secure payment processing.
How Does Rev Handle Data Privacy?
Rev takes data privacy very seriously. We do not sell customer data or allow for customer data to be used to train external LLMs, ensuring your content remains private.
Can I Control Who Has Access to My Files on Rev?
Yes, Rev provides robust file sharing and permission controls. With workspaces and file permissions, users can grant or revoke access within file access controls.
How Does Rev vet Its Freelance Transcriptionists?
Rev implements a rigorous verification process for our freelance transcriptionists. This includes ID verification and requiring all transcriptionists to sign Non-Disclosure Agreements (NDAs). We also conduct continual checks to ensure ongoing compliance and quality.
What Should I Do If I Suspect a Security Breach on My Account?
If you suspect a security breach, contact Rev's support team immediately. Our Security Team is on call 24/7 to respond to security alerts and incidents.
Does Rev Offer Enterprise-Level Security Features?
Yes, Rev offers several enterprise-level security features. These include SSO enforcement, domain claiming, MFA, and the ability to configure organization-wide sharing permissions.